Managing firewalls using iptables can be powerful but intimidating—especially for new users. The syntax is often complex, and even small mistakes can lock you out of your own system.
To help with this, I built a Bash-based interactive tool called IPTables Wizard, designed to simplify the process of creating and managing iptables firewall rules directly from your terminal.
What is IPTables Wizard?
IPTables Wizard is a shell script that helps you build firewall rules interactively using a simple terminal menu. It’s ideal for sysadmins, network administrators, or regular users who want precise control over traffic filtering on their Linux systems.
Key Features
- Built-in presets for common services (SSH, HTTP, HTTPS, FTP, DNS, etc.)
- Sub-options for each preset: allow, drop, allow from source, drop from source
- Custom rule builder (INPUT, OUTPUT, FORWARD, PREROUTING/NAT)
- Option to flush existing rules and reset default policies
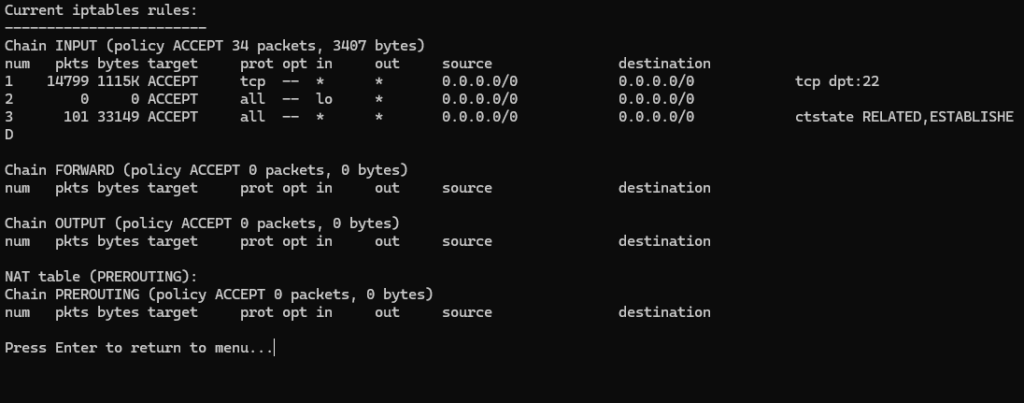
- View current rules via
iptables -L -v -n - Rule preview before applying
- Save rules to file for reuse
Requirements
- Linux system with
iptablesinstalled - Root access
- Bash shell
Installation & Usage
- Clone the repository:
git clone https://github.com/ryanachmad12/IPTables-Wizard-Term.git cd IPTables-Wizard-Term- Make the script executable:
chmod +x main.sh- Run the script as root:
sudo ./main.sh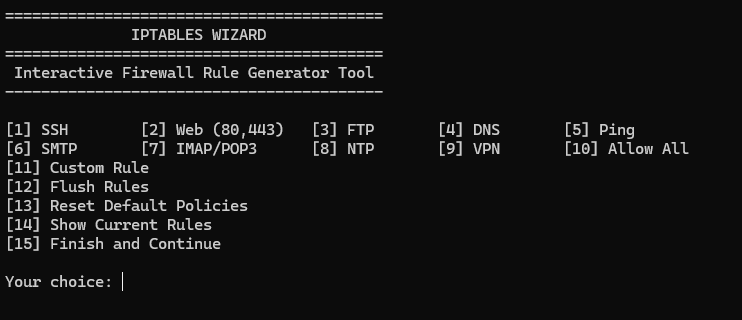
For Example I try to run for SSH:
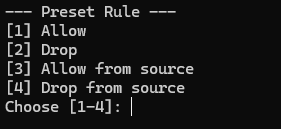
We try to select allow and when done will be directed to the main menu and can be checked for iptables in the “Finish and Continue” section:
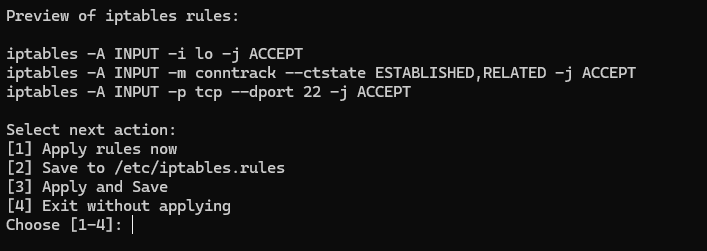
And try to apply to directly use the added rule, then to check the rules that we installed can use the “Show Current Rules” option:
Menu Navigation
Once you launch the script, you’ll be presented with an interactive menu containing:
- SSH (port 22)
- Web (port 80/443)
- FTP
- DNS
- Ping (ICMP)
- Mail, VPN, NTP, and more
- Custom rule builder
- Flush rules
- Reset policies
- View current rules
- Apply & Save
Each preset supports:
- Allow
- Drop
- Allow from specific source
- Drop from specific source
You can also build custom rules by specifying protocol, port, and optional source IP/CIDR.
Example Generated Rules
If you allow SSH from a specific IP (e.g. 192.168.0.100), the script generates:
iptables -A INPUT -p tcp -s 192.168.0.100 --dport 22 -j ACCEPT
If you choose to drop UDP DNS requests:
iptables -A INPUT -p udp --dport 53 -j DROP
Before applying, you will have the chance to preview all generated rules.
Apply & Save Options
After rule configuration, you can choose to:
- Apply rules immediately
- Save to a file (
/etc/iptables.rules) - Apply and save
- Exit without applying
Saved rules can later be restored using iptables-restore.
Why Use This Tool?
This script reduces the risk of human error and speeds up firewall setup. It’s lightweight and perfect for quick deployment, testing, or educational use. You get full control with less complexity.
GitHub Repository
Project source code:
Official iptables manual (used as reference):
Author
Ryan Achmad
Website: https://opslinuxsec.com
Blog: https://blog.opslinuxsec.com
GitHub: https://github.com/ryanachmad12
Disclaimer
Use this tool at your own risk. Incorrect firewall configurations may result in loss of access or exposure of services. Always review and understand the rules before applying them.
