Chinese RJ45-USB With Flash Memory .exe Recognized as Malware
Chinese RJ45-USB With Flash Memory .exe Recognized as Malware
Overview
On January 12th, I encountered an unusual behavior when plugging in a Chinese-made RJ45-USB adapter into my PC. Instead of simply establishing a network connection, the device was recognized as external storage. This storage contained an executable (.exe) file, which Windows prompted to auto-run. After further investigation, the file was flagged as malware by multiple sandboxes. This led to a series of questions about the security risks and implications of such a device.
The Issue
-
Unexpected Storage on Network Adapter: RJ45 adapters do not require flash memory or storage for their intended purpose. It was concerning to find that this adapter had an executable file stored on it.
-
Suspicion of Malware: The .exe file, upon analysis, was detected as 100% malicious by various sandbox services such as VirusTotal, Hybrid, and ANY.RUN. The file contained Russian language elements and was recognized as potentially dangerous.
-
Device Behavior: Upon testing, the device also exhibited strange behavior, including quickly draining a fully charged device battery, suggesting that it may have been running hidden processes—potentially related to data exfiltration or communication with a command-and-control (C&C) server.
Key Questions
-
Is it a security risk? Yes, storing and executing an unknown file on a network adapter is a significant security concern.
-
Can it be weaponized? Yes, this kind of hardware can be used to deliver malware or facilitate attacks.
-
Does this pose a national security risk? Given the context, it is a valid concern, especially when considering the possibility of such devices being used in cyber warfare.
Community Response
Despite the findings, many so-called experts on social media platforms ridiculed the post without offering any constructive analysis. However, the broader community, including those with technical knowledge, recognized the potential risks and supported the investigation. This highlights the importance of staying vigilant and questioning any suspicious behavior in hardware devices.

I did not "claim" or "state" from myself directly, I said "recognized as malware" (as per automated analysis from sites), let's learn properly understand the things we read, before "hater expert readers" jump into conclusions. Because the questions I was asking is not "is this malware or not", the questions I did ask across multiple occasions and we should all ask, and some intelligence individuals did just that, is:
Is storage on RJ45 a security risk? = Yes What is a storage doing on an RJ45?, that should not be there Can this be weaponized? = Yes.
Is this a security concern for national security? Most definitely Yes. It seems the self-proclaimed experts that were recommended by their colleagues on X, and I eagerly awaited their analysis, but they provided none at all. Instead, they resorted to criticism filled with hateful comments and vile insults, "making fun of me", questioning everything from my intelligence to my professionalism—and everything in between. Placing my Twitter account on "fraud" lists and engaging in other baseless troll-attacks, and the funniest one of all, counting with expressed anger, how much money I make from the courses I offer, and wishing me to starve 🎂 . Some even went as far as suggesting I should "step down as CEO of EPCYBER" ..but how can I step down from my own house?!? 🤦🏻♀️

Supplier's Statement
Interestingly, the Chinese supplier of the device responded by stating, "You chose the wrong supplier." While they didn’t outright deny the findings, this statement suggests an acknowledgment of the risks, even if indirectly.
What Did We Learn?
-
The Bigger Picture: While China produces high-quality products, not everything manufactured there is necessarily benign. The risks posed by such devices should not be underestimated, especially in sensitive or critical systems.
-
Stay Vigilant: Always question the integrity of devices that you buy, particularly when they have features or behaviors that are not clearly documented or understood.
-
Proactive Security: It’s crucial to be proactive about security and not wait for real-world incidents to occur before addressing such risks.
Additional Insights
-
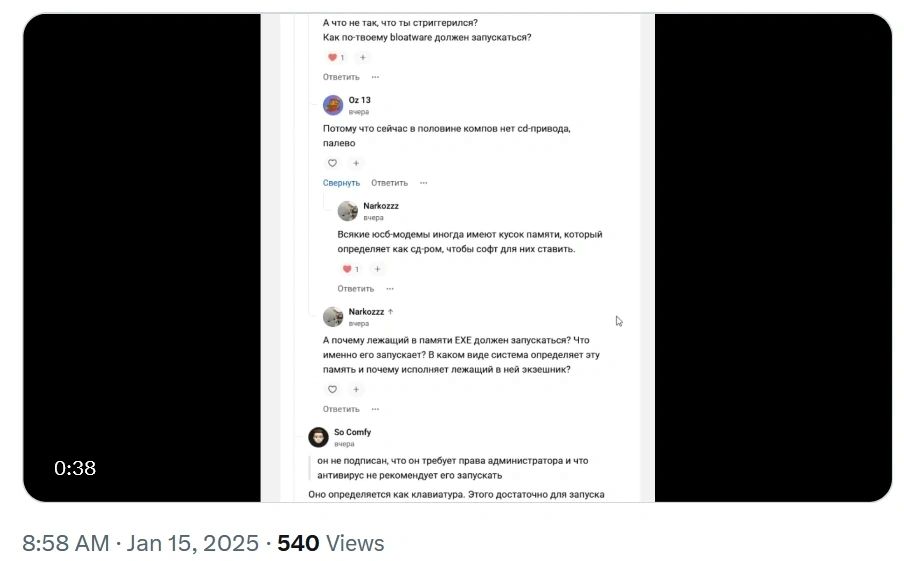
Forum Discussions: Experts and malware analysts in specialized forums have discussed similar cases, reinforcing the concern about devices that combine network functionality with hidden storage features.
-
Social Media Backlash: Despite the backlash from some individuals, the majority of readers and community members understand the risks involved and appreciate the findings.
Conclusion
- The Risk is Real: I am confident that this device presents a real security risk.
- Awareness: We need to be more aware of the potential vulnerabilities posed by seemingly innocuous devices.
- Lessons Learned: While the device was inexpensive, the hidden risks far outweigh the cost savings. Always be cautious when buying unfamiliar hardware, and do your research.
Further Reading
-
You can explore detailed discussions and analysis of this topic in specialized forums and other technical platforms.
-
Full link to the discussion: Forum Discussion on X
Note: I have removed this adapter from all my devices, and I strongly advise others to avoid using it or similar devices without fully understanding the potential risks.
Stay safe and keep questioning everything! :)
